Initial Enumeration
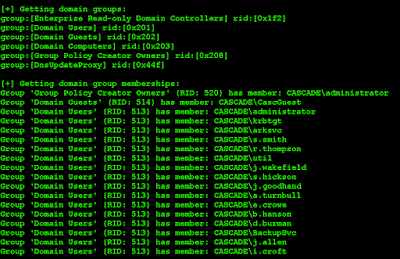
Running enum4linux we can find lots of good information, like
- Domain Name
- User list
- Local group membership
- Domain group membership
With a first run of Impacket tools we don't find any user that don't require Kerberos Pre-Auth
But a run of ldapsearch against the domain with simple authentication (-x) and with a little guessing about the TLD of the domain (the most used suffixes are lan, loc,local)
ldapsearch -x -b "dc=CASCADE,dc=local" -H ldap://10.10.10.182
We find the user r.thompson has a legacy attribute in LDAP/AD named cascadeLegacyPwd.
The base64 value is decoded to the password: rY4n5eva
Unfortunately this user is not part of "remote management" User so we can't get a shell, but we can look into SMB shares
Inside them we can find some files:
- an output of dcdiag
- a meeting note
- a log of Ark for AD (ARK is Admin Report Kit for AD)
- An export of registry for VNC installation (VNC install.reg)
The meeting note:
The ARK report:
It looks like there were two users Test and TempAdmin that were deleted
And there's also the VNC install registry entry:
We have a password field that need to be decrypted with a tool by Luigi Auriemma:
Initial Foothold & User Flag
We have a password sT333ve2, and with a bit of scripting we can find it's valid for user s.smithThis can be used for winrm:
Root Flag
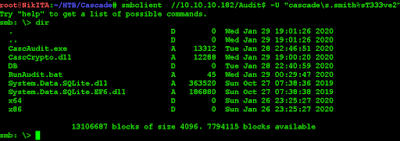
With the user s.smith we can access Audit$ share (with r.thompson it was not possible)The interesting part is in DB folder and it's a sqlite database
In the database there a base64 value that could be a password for user arkvc, but it's probably encrypted
Let's get the executable and dcompiled it (dnspy is good for this)
Then see the decryption call that uses c4scadek3y654321 as AES 128 bit key
And in the DLL ther eis the section with the Initialization Vector for AES 128:
Putting the three things: ciphertext, key, IV in an online tool:
We get the password for arksvc: w3lc0meFr31nd
Next step is to use it to enter the box as arksvc:
But there is nothing interesting to find.
One option is to look for the deleted objects in AD with the command:
ldapsearch -w w3lc0meFr31nd -H ldap://10.10.10.182 -b 'CN=Deleted Objects,DC=cascade,DC=local' -E '!1.2.840.113556.1.4.417' -s sub '(objectClass=*)' -D "CN=ArkSvc,OU=Services,OU=Users,OU=UK,DC=cascade,DC=local"
And we get the "CascadeLegacyPwd" attribute:
The encoded value is YmFDVDNyMWFOMDBkbGVz
The decoded value is: baCT3r1aN00dles
Remembering the first meeting node we can try to get access as administrator:


















No comments:
Post a Comment
Note: Only a member of this blog may post a comment.