Running enum4linux gives many of "access denied" errors.
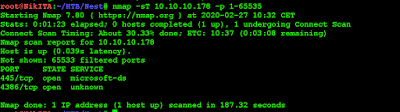
Nmap shows a couple of open ports:
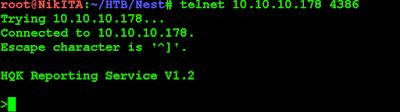
Port 4386 looks interesting
But before exploring it let's focus on port 445 using smbclient:
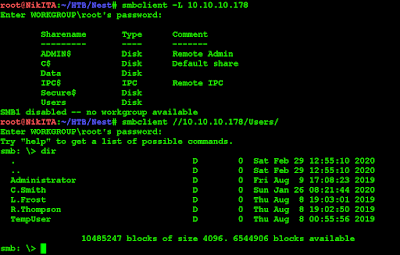
With no authentication we can see that there are two non standard shares: Data and Users.
Users share reveals some of the users that might be using the system: unfortunately these folders are not accessible
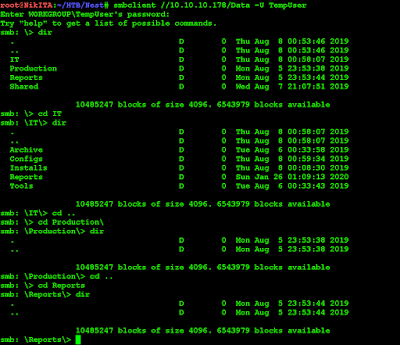
Let's turn to Data share:
There are some folders that are not accessible.
The only accessible folder is Shared (obviously!)
There are some subfolders and we have to explore the content.
We can get a couple of files and see their content:
User Escalation
Trying with the credentials we can see that there is nothing interesting in Users share:There are some subfolders in IT, but the most interesting is the "Configs/NotepadPlusPlus"
So let's connect to Secure$ share and look into folder "IT\Carl"
There is Visual studio project named "RUScanner" inside WIP subfolder
Using "prompt" "recurse" and "mget" we can copy the full folder to our computer t
Remembering the prevoius folders and share we can also look into the share "Data"
There is a subfolder "it\Configs\RU Scanner" that contains a RU_config.xml that is related to the Visual studio project:
The RU_config.xml contains an encrypted password for user c.smith
Inside the project there is an Utils.vb file that contains a couple of encrypt/decrypt functions with encoded parameters:
Now let's use it to connect to "users" share as c.smith:
There is the user flag and another folder named "HQK Reporting".
User flag is: cf71b25404be5d84fd827e05f426e987
Root Escalation
Let's start downloading the Folder named "HQK Reporting".This looks something related to the application running on port tcp/4386 because there is xml file with this content:
in "A Integration Module" there is an executable "Hqkldap.exe" file but it doesn't look useful for now, but it will be later.
Instead "Debug Mode Password" looks void but it has a hidden content in an alternate stream (that's a feature in NTFS filesystem).
This hidden stream can be show with allfile command in sbmclient session:
After getting it we can see the content:
Debug Password is: WBQ201953D8w
Let's connect to port 4386 and try typing HELP command:
There are a few commands, that after trying them:
- LIST shows the content of the current folder
- SETDIR changes the current folder
- RUNQUERY executes a query
- DEBUG enter debug mode
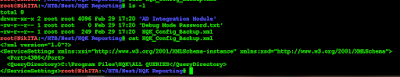
It is running in "c:\program files\HQK\ALL QUERIES".
We can also move to parent directory with "SETDIR .."
Then list the content of the folder with "LIST"
And finally show the content of the file HQK_Config.xml with "SHOWQUERY 3"
Entering the LDAP folder we can see a LDAP.conf file with inside the password for administrator user but it is encrypted in some way.
We can open it with a .NET debugging tool like dnSpy
And we can open the Main() part of the executable
We can see that it checks that
- there is a parameter at command line
- it check for existance of Hqkdbimport.exe
After that it opens the file given as first argument and read username, password and domain
After that it uses the paramters to connect to LDAP.
The idea here is to leverage the debugging editing feature to
- bypass the check for HQKdbimport.exe
- print out the decrypted password
we can do that just by editing the code and saving it as an additional executable
Next we can use it to connect to c$ and get root flag:



























No comments:
Post a Comment
Note: Only a member of this blog may post a comment.