System Information
Enumeration
Since it's a Windows box, I started running enum4linux and got some informationThe domain name is MEGABANK
There are 8 users
And the standard Builtin groups
Initial Foothold and User Flag
I created a file with usernames and I tried to use bruteforce password using the rockyou wordlist for some time, but with no luckI then decided to use check if the administrator of the domain was lazy and not aware of basic security hygiene: I bruteforced using also usernames in the password list, with a stupid bash script:
for user in $(cat user.txt)
do
echo "Trying $user"
smbclient -L 10.10.10.172 -U MEGABANK/$user%$user 2>/dev/null
done
And I discovered that SABatchJobs is valid password for SABatchJobs user:
This file contained a cleartext password: 4n0therD4y@n0th3r$
Unfortunately the user mhope didn't have access to administrative shares like ADMIN$, C$, E$
And the other shares didn't reveal additional folders or files.
With the mhope account I enumerated a bit more the domain groups:
And also connect through WinRM session as mhope and got user flag
Root escalation
With the means of WinPEAS I found that
- Antivirus was not installed
- There were backup of the SAM in C:\Windows\System32\config\RegBack but access was denied
The user mhope is member of some groups:
The fact that mhope is in "Azure Admin" made me think that it can be possible to exploit something.
Infact this machine is running an Azure ADConnect service. This service is used to sync local on-prem AD to Azure AD in hybrid cloud environments.
To do that it needs to use a high privilege account and there is a known exploit that uncovers credentials of this accounts.
It is explained in great details here:
https://www.youtube.com/watch?v=JEIR5oGCwdg
https://blog.xpnsec.com/azuread-connect-for-redteam/
https://vbscrub.video.blog/2020/01/14/azure-ad-connect-database-exploit-priv-esc/
The last one provides an executable ready to use:
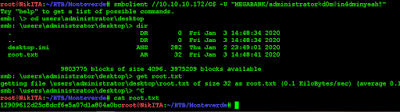
So the administrator password is: d0m@in4dminyeah!
With this password it's easy to get root flag and a WinRM shell:












No comments:
Post a Comment
Note: Only a member of this blog may post a comment.